Point-to-site authentication methods
The user must be authenticated before Azure accepts a P2S VPN connection. There are two mechanisms that Azure offers to authenticate a connecting user.
Authenticate using native Azure certificate authentication
When using the native Azure certificate authentication, a client certificate on the device is used to authenticate the connecting user.
Client certificates are generated from a trusted root certificate and then installed on each client computer.
- You can use a root certificate that was generated using an Enterprise solution, or you can generate a self-signed certificate.
The validation of the client certificate is performed by the VPN gateway and happens during establishment of the P2S VPN connection.
- The root certificate is required for the validation and must be uploaded to Azure.
Authenticate using native Azure Active Directory authentication
Azure AD authentication allows users to connect to Azure using their Azure Active Directory credentials. Native Azure AD authentication is only supported for:
- OpenVPN protocol
- Windows 10
- Requires the use of the Azure VPN Client.
With native Azure AD authentication, you can leverage Azure AD's conditional access as well as multifactor authentication (MFA) features for VPN.
At a high level, you need to perform the following steps to configure Azure AD authentication:
- Configure an Azure AD tenant
- Enable Azure AD authentication on the gateway
- Download and configure Azure VPN Client
Authenticate using Active Directory (AD) Domain Server
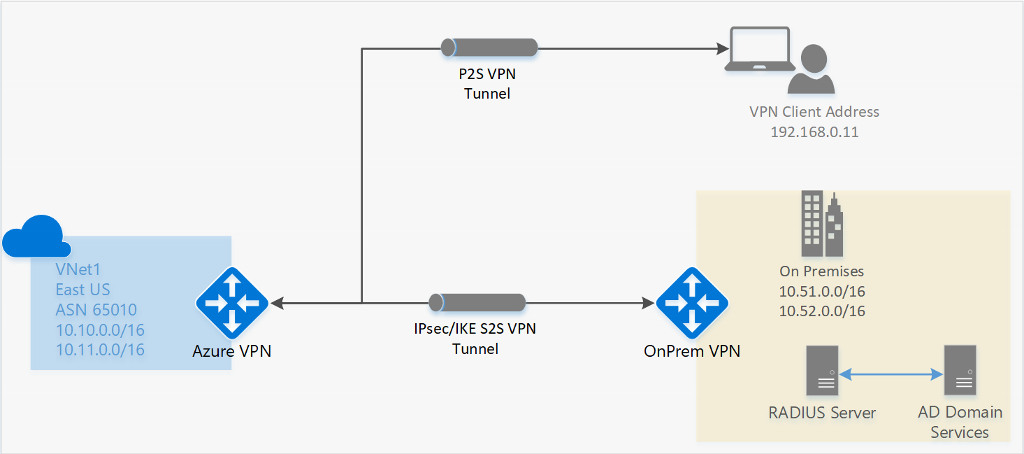
AD Domain authentication is a popular option because it allows users to connect to Azure using their organization domain credentials. It requires a RADIUS server that integrates with the AD server. Organizations can also leverage their existing RADIUS deployment.
The RADIUS server is deployed either on-premises or in your Azure VNet.
During authentication, the Azure VPN Gateway passes authentication messages back and forth between the RADIUS server and the connecting device. Thus, the Gateway must be able to communicate with the RADIUS server.
WARNING
If the RADIUS server is present on-premises, then a VPN S2S connection from Azure to the on-premises site is required for reachability.
The RADIUS server can also integrate with AD certificate services. This lets you use the RADIUS server and your enterprise certificate deployment for P2S certificate authentication as an alternative to the Azure certificate authentication.
Integrating the RADIUS server with AD certificate services means that you can do all your certificate management in AD, you don’t need to upload root certificates and revoked certificates to Azure.
A RADIUS server can also integrate with other external identity systems. This opens many authentication options for P2S VPN, including multi-factor options.
 1500bytes
1500bytes