VPN Gateway configuration requirements
The following table lists the requirements for PolicyBased and RouteBased VPN gateways. This table applies to both the Resource Manager and classic deployment models.
For the classic model, PolicyBased VPN gateways are the same as Static gateways, and Route-based gateways are the same as Dynamic gateways.
| Features | PolicyBased Basic VPN Gateway | RouteBased Basic VPN Gateway | RouteBased Standard VPN Gateway | RouteBased High Performance VPN Gateway |
|---|---|---|---|---|
| Site-to-Site connectivity (S2S) | PolicyBased VPN configuration | RouteBased VPN configuration | RouteBased VPN configuration | RouteBased VPN configuration |
| Point-to-Site connectivity (P2S) | Not supported | Supported (Can coexist with S2S) | Supported (Can coexist with S2S) | Supported (Can coexist with S2S) |
| Authentication method | Pre-shared key | Pre-shared key for S2S connectivity, Certificates for P2S connectivity | Pre-shared key for S2S connectivity, Certificates for P2S connectivity | Pre-shared key for S2S connectivity, Certificates for P2S connectivity |
| Maximum number of S2S connections | 1 | 10 | 10 | 30 |
| Maximum number of P2S connections | Not supported | 128 | 128 | 128 |
| Active routing support (BGP) (*) | Not supported | Not supported | Supported | Supported |
WARNING
BGP is not supported for the classic deployment model.
Create the VPN Gateway
The VPN gateway settings that you chose are critical to creating a successful connection.
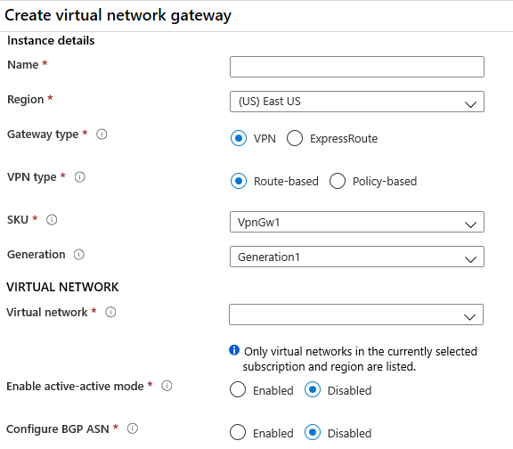
Gateway type.
- VPN
- ExpressRoute
VPN Type
Route based
- Most VPN types are Route-based.
- The type of VPN you choose depends on the make and model of your VPN device, and the kind of VPN connection you intend to create.
- Typical route-based gateway scenarios include point-to-site, inter-virtual network, or multiple site-to-site connections.
- Route-based is also selected when you coexist with an ExpressRoute gateway or if you need to use IKEv2.
Policy based
- Policy-based gateways support only IKEv1.
SKU
- Use the drop-down to select a gateway SKU.
- Your choice will affect the number of tunnels you can have and the aggregate throughput benchmark.
- The benchmark is based on measurements of multiple tunnels aggregated through a single gateway. It is not a guaranteed throughput due to Internet traffic conditions and your application behaviors.
Generation
- Generation1
- Basic and VpnGw1 SKUs are only supported in Generation1.
- Generation2.
- VpnGw4 and VpnGw5 SKUs are only supported in Generation2.
WARNING
You cannot change generations or SKUs across generations.
Virtual Networks
- The virtual network that will be able to send and receive traffic through the
Virtual network gateway
- A virtual network cannot be associated with more than one gateway.
TIP
You can view the IP address assigned to the gateway. The gateway should appear as a connected device.
Gateway subnet
VPN Gateways require a gateway subnet. You can create a Gateway subnet before you create a VPN gateway, or you can create it during the creation of the VPN Gateway.
TIP
The gateway subnet contains the IP addresses that the virtual network gateway VMs and services use.
When you create your virtual network gateway, gateway VMs are deployed to the gateway subnet and configured with the required VPN gateway settings.
WARNING
Never deploy anything else (for example, additional VMs) to the gateway subnet.
WARNING
The gateway subnet must be named GatewaySubnet to work properly. Naming the gateway subnet GatewaySubnet tells Azure that this is the subnet to deploy the virtual network gateway VMs and services to.
When you create the gateway subnet, you specify the number of IP addresses that the subnet contains. The IP addresses in the gateway subnet are allocated to the gateway VMs and gateway services. Some configurations require more IP addresses than others.
When you are planning your gateway subnet size, refer to the documentation for the configuration that you are planning to create. For example, the ExpressRoute/VPN Gateway coexist configuration requires a larger gateway subnet than most other configurations. Additionally, you may want to make sure your gateway subnet contains enough IP addresses to accommodate possible future additional configurations.
While you can create a gateway subnet as small as /29, we recommend that you create a gateway subnet of /27 or larger (/27, /26 etc.) if you have the available address space to do so. This will accommodate most configurations.
Create the Local Network Gateway
The local network gateway typically refers to the on-premises location. You give the site a name by which Azure can refer to it, then specify the IP address or FQDN of the on-premises VPN device for the connection.
You also specify the IP address prefixes that will be routed through the VPN gateway to the VPN device. The address prefixes you specify are the prefixes located in the on-premises network.
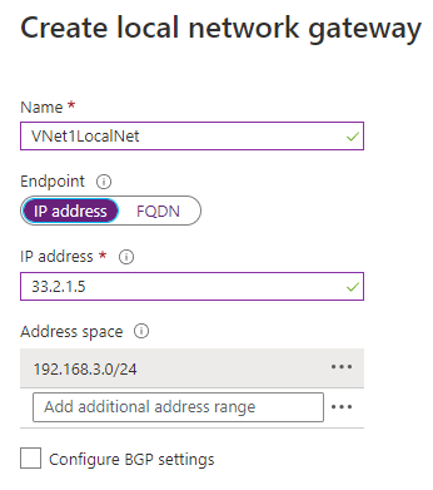
IP Address
- The public IP address of the local gateway.
Address Space
- One or more IP address ranges (in CIDR notation) that define your local network's address space.
If you plan to use this local network gateway in a BGP-enabled connection, then the minimum prefix you need to declare is the host address of your BGP Peer IP address on your VPN device.
Configure the on-premises VPN device
There is a validated list of standard VPN devices that work well with the VPN gateway. This list was created in partnership with device manufacturers like Cisco, Juniper, Ubiquiti, and Barracuda Networks.
When your device is not listed in the validated VPN devices table, the device may still work. Contact your device manufacturer for support and configuration instructions.
To configure your VPN device, you will need:
A shared key
- The same shared key that you specify when creating the VPN connection.
The public IP address of your VPN gateway
- The IP address can be new or existing.
TIP
Depending on the VPN device that you have, you may be able to download a VPN device configuration script .
Create the VPN Connection
Once your VPN gateways are created, you can create the connection between them. If your VNets are in the same subscription, you can use the portal.
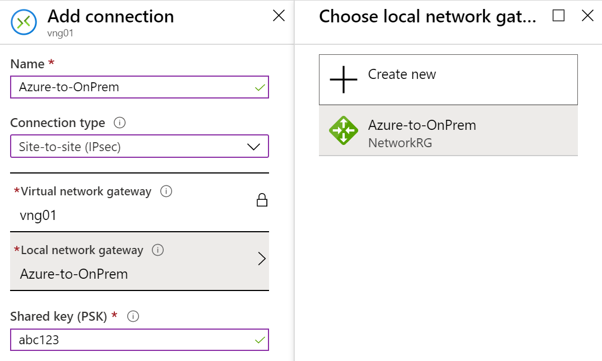
Name
- Enter a name for your connection.
Connection type
- Select Site-to-Site (IPSec) from the drop-down.
Shared key (PSK). In this field, enter a shared key for your connection. You can generate or create this key yourself. In a site-to-site connection, the key you use is the same for your on-premises device and your virtual network gateway connection.
Verify the VPN Connection
After you have configured all the Site-to-Site components, it is time to verify that everything is working. You can verify the connections either in the portal, or by using PowerShell.
Connect networks with Site-to-site VPN connections
A site-to-site (S2S) VPN gateway connection lets you create a secure connection to your virtual network from another virtual network or a physical network. The following diagram illustrates how you would connect an on-premises network to the Azure platform. The internet connection uses an IPsec VPN tunnel.
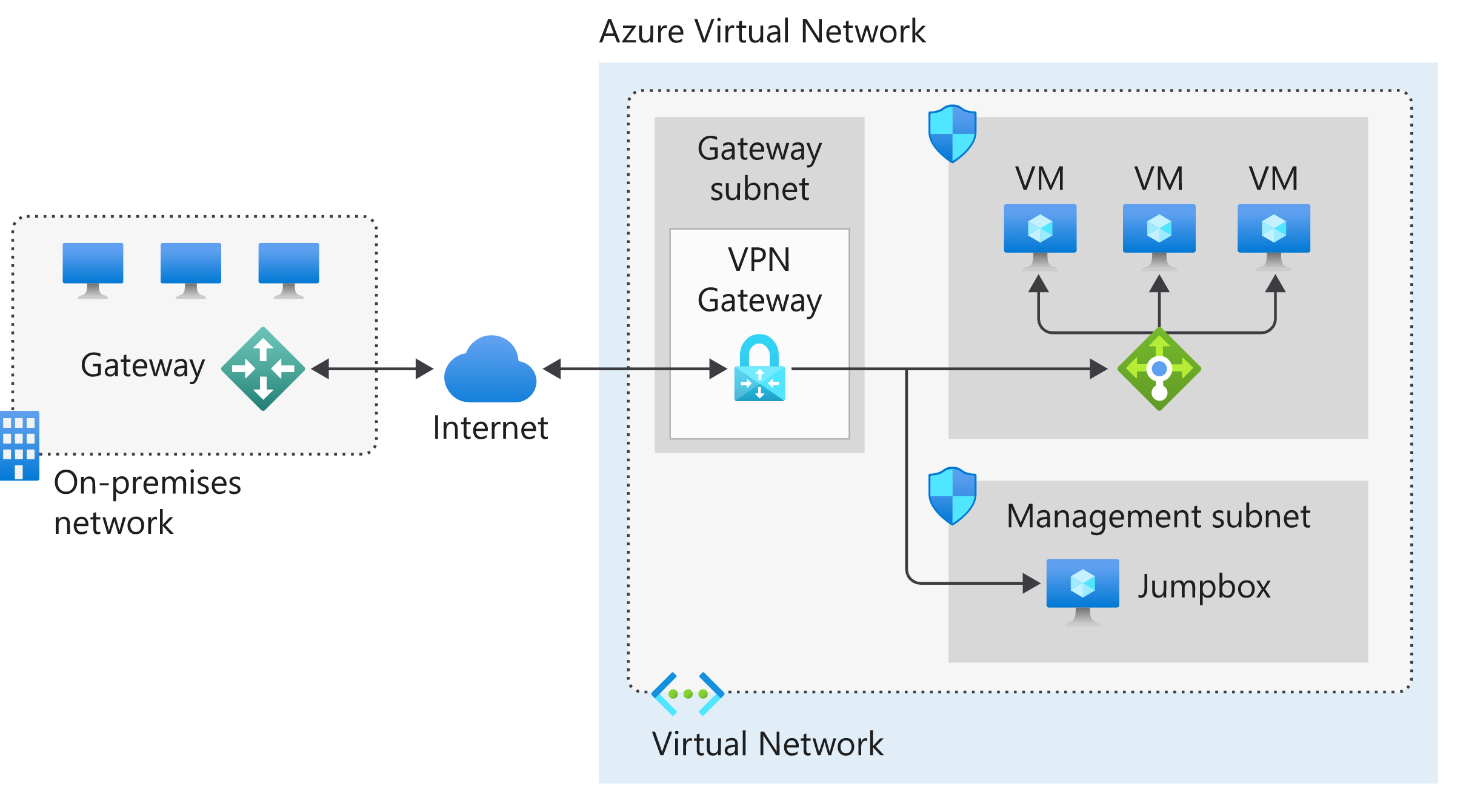
In the diagram:
The on-premises network represents your on-premises Active Directory and any data or resources.
The gateway is responsible for sending encrypted traffic to a virtual IP address when it uses a public connection.
The Azure virtual network holds all your cloud applications and any Azure VPN gateway components.
An Azure VPN gateway provides the encrypted link between the Azure virtual network and your on-premises network. An Azure VPN gateway is made up of these elements:
- Virtual network gateway
- Local network gateway
- Connection
- Gateway subnet
Cloud applications are the ones you've made available through Azure.
An internal load balancer, located in the front end, routes cloud traffic to the correct cloud-based application or resource.
Using this architecture offers several benefits, including:
Configuration and maintenance are simplified.
Having a VPN gateway helps ensure that all data and traffic are encrypted between the on-premises gateway and the Azure gateway.
The architecture can be scaled and extended to meet your organization's networking needs.
This architecture isn't applicable in all situations because it uses an existing internet connection as the link between the two gateway points. Bandwidth constraints can cause latency issues that result from reuse of the existing infrastructure.
Configure point-to-site clients
Users use the native VPN clients on Windows and Mac devices for P2S.
TIP
Azure provides a VPN client configuration zip file that contains settings required by these native clients to connect to Azure.
For Windows devices, the VPN client configuration consists of an
installer packagethat users install on their devices.For Mac devices, it consists of the
mobileconfigfile that users install on their devices.
The zip file also provides the values of some of the important settings on the Azure side that you can use to create your own profile for these devices.
Some of the values include:
- VPN gateway address
- Configured tunnel types
- Routes
- Root certificate for gateway validation.
INFO
That for Windows clients, you must have administrator rights on the client device to initiate the VPN connection from the client device to Azure.
Connect devices to networks with Point-to-site VPN connections
A Point-to-Site (P2S) VPN gateway connection lets you create a secure connection to your virtual network from an individual client computer.
A P2S connection is established by starting it from the client computer. This solution is useful for telecommuters who want to connect to Azure VNets from a remote location, such as from home or a conference.
P2S VPN is also a useful solution to use instead of S2S VPN when you have only a few clients that need to connect to a VNet.
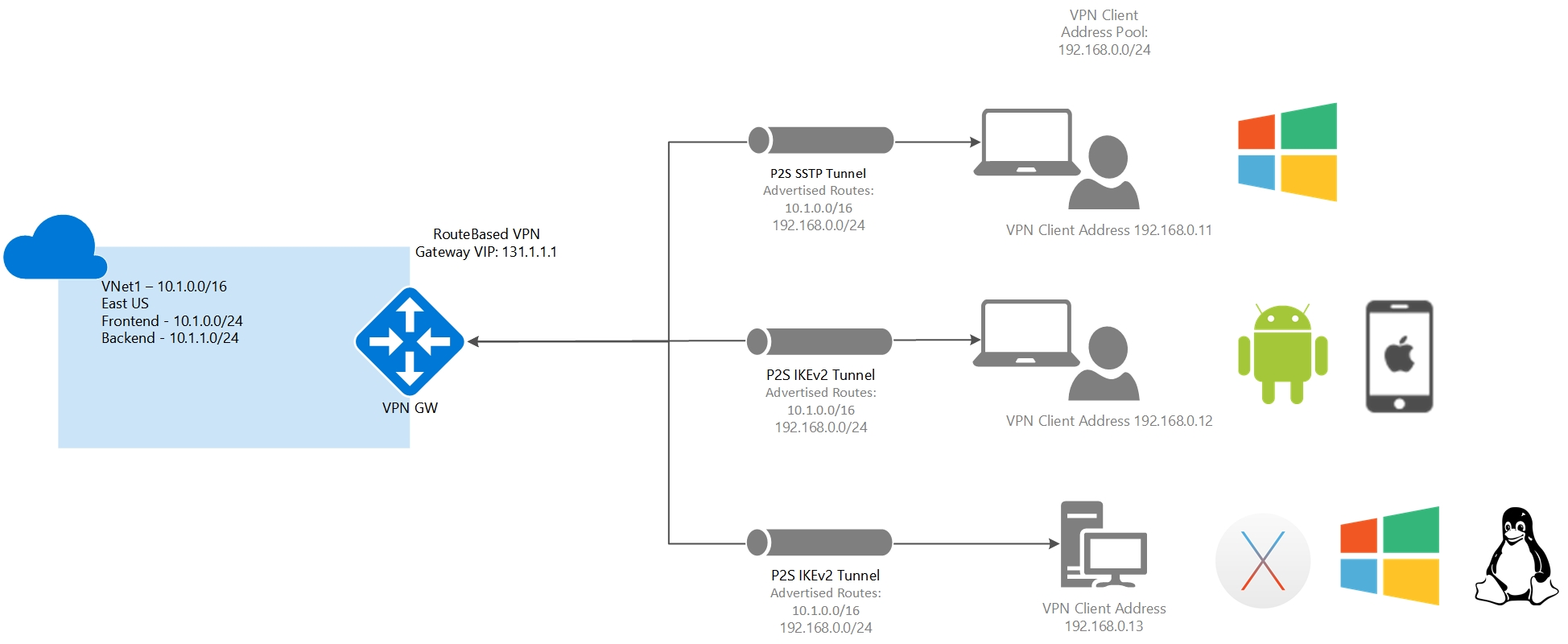
Point-to-site protocols
Point-to-site VPN can use one of the following protocols:
- OpenVPN® Protocol
- SSL/TLS based VPN protocol.
- A TLS VPN solution can penetrate firewalls, since most firewalls open TCP port 443 outbound, which TLS uses.
- OpenVPN can be used to connect from Android, iOS (versions 11.0 and above), Windows, Linux, and Mac devices (macOS versions 10.13 and above).
- Secure Socket Tunneling Protocol (SSTP)
- Proprietary TLS-based VPN protocol.
- A TLS VPN solution can penetrate firewalls, since most firewalls open TCP port 443 outbound, which TLS uses.
- SSTP is only supported on Windows devices. Azure supports all versions of Windows that have SSTP (Windows 7 and later).
- IKEv2 VPN
- Standards-based IPsec VPN solution.
- IKEv2 VPN can be used to connect from Mac devices (macOS versions 10.11 and above).
 1500bytes
1500bytes